
The Vice Society ransomware gang is deploying a new, rather sophisticated PowerShell script to automate data theft from compromised networks.
Stealing corporate and customer data is a standard tactic in ransomware attacks for use as further leverage when extorting victims or reselling the data to other cybercriminals for maximum profit.
Vice Society's new data exfiltrator is fully automated and uses "living off the land" binaries and scripts that are unlikely to trigger alarms from security software, keeping their activities stealthy before the final step of the ransomware attack, the encrypting of data.
PowerShell exfiltration
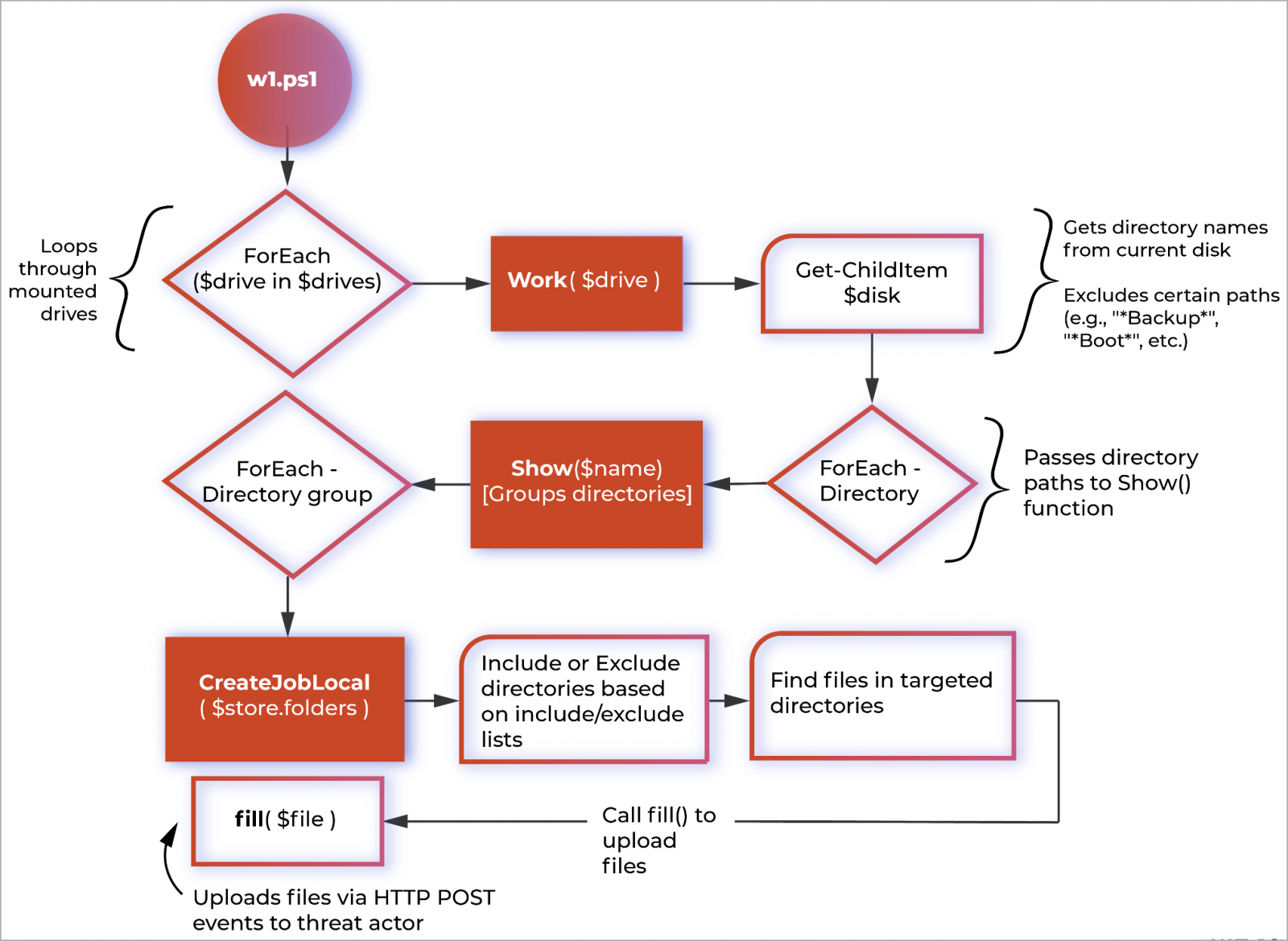
The new data theft tool was discovered by Palo Alto Networks Unit 42 during an incident response in early 2023, when the responders recovered a file named "w1.ps1" from a victim's network and, more specifically, referenced in an Event ID 4104: Script Block Logging event.
The script uses PowerShell to automate data exfiltration and consists of multiple functions, including Work(), Show(), CreateJobLocal(), and fill().
These four functions are used to identify potential directories for exfiltration, process groups of directories, and eventually exfiltrate data via HTTP POST requests to Vice Society's servers.
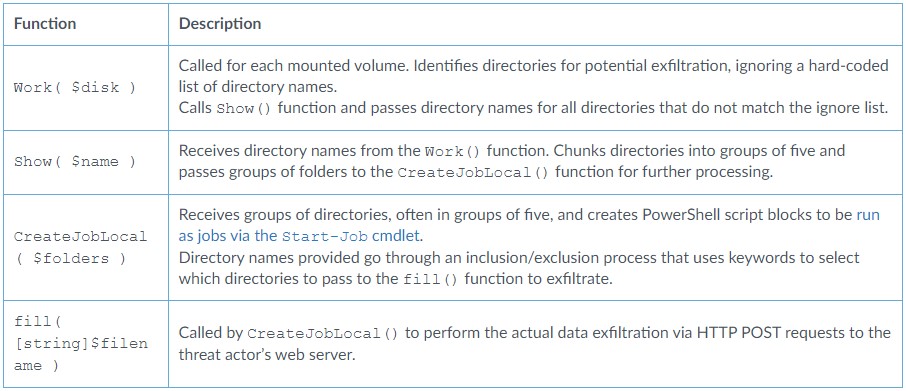
"The script does not require any arguments, as the onus of what files to copy out of the network is left to the script itself," notes Unit 42 in the report.
"Testing confirmed that the script ignores both files that are under 10 KB in size and those that do not have a file extension."
While there appears to be some automated functionality in the script to determine what files are stolen, there is still a master exclusion and inclusion list to help refine what files are stolen.
For example, the script will not steal data from folders whose names include common strings for backups, program installation folders, and Windows operating system folders.
However, it will specifically target folders containing over 433 strings in English, Czech, German, Lithuanian, Luxembourgish, Portuguese, and Polish, emphasizing German and English.
For example, some of the folders it targets include:
*941*", "*1040*", "*1099*", "*8822*", "*9465*", "*401*K*", "*401K*", "*4506*T*", "*4506T*", "*Abkommen*", "*ABRH*", "*Abtretung*", "*abwickeln*", "*ACA*1095*", "*Accordi*", "*Aceito*", "*Acordemen*", "*Acordos*", "*Acuerde*", "*Acuerdo*", "*Addres*", "*Adres*", "*Affectation*", "*agreem*", "*Agreemen*Disclosur*", "*agreement*", "*Alamat*", "*Allocation*", "*angreifen*", "*Angriff*", "*Anmeldeformationen*", "*Anmeldeinformationen*", "*Anmeldenunter*", "*Anmeldung*", "*Anschrift*", "*Anspruch*", "*Ansspruch*", "*Anweisung*", "*AnweisungBank*", "*anxious*", "*Análise*", "*Apotheke*", "*ARH*", "*Asignación*", "*Asignatura*", "*Assegnazione*", "*Assignation*", "*Assignment*", "*Atribuição*", "*attorn*", "*Audit*", "*Auditnaadrese*", "*Aufführen*", "*Aufgabe*", "*Aufschühren*", "*Auftrag*", "*auftrunken*", "*Auftrunkinen*", "*Auswertung*", "*Avaliação*", "*Avaliações*", "*Avtal*", "*balanc*", "*bank*", "*Bargeld*", "*Belästigung*", "*Benef*", "*benefits*", "*Bericht*", "*Beschäftigung*", "*Betrug*", "*Bewertung*", "*bezahlen*", "*billing*", "*bio*"
The PowerShell script uses system-native cmdlets like “Get-ChildItem” and “Select-String” to search and exfiltrate data from the infected machine, minimizing its footprint and maintaining a stealthy profile.
Another interesting aspect of Vice Society’s new data exfiltrator is its rate-limiting implementation that sets a max of 10 simultaneously running jobs of five directory groups to avoid capturing too much of the host’s available resources.
Although the specific goal behind this is unclear, Unit 42 comments that it aligns with best coding practices and shows a professional level of script coding.
Vice Society evolving
Vice Society’s new data exfiltration script uses “living off the land” tools to evade detection from most security software and features multi-processing and process queuing to keep its footprint small and its activity stealthy.
Unit 42 comments that this approach makes detection and hunting challenging, although the security researchers have provided advice on that front at the bottom of their report.
In December 2022, SentinelOne warned about Vice Society having switched to a new, sophisticated file encryptor dubbed “PolyVice,” which was probably supplied by a contracted developer who also sold his malware to Chilly and SunnyDay ransomware.
Unfortunately, with the adoption of ever-sophisticated tools, Vice Society has become a more formidable threat to organizations worldwide, giving defenders fewer opportunities to detect and stop the attacks.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now