
A custom Flipper Zero firmware called 'Xtreme' has added a new feature to perform Bluetooth spam attacks on Android and Windows devices.
A security researcher previously demonstrated the technique against Apple iOS devices, inspiring others to experiment with its potential impact on other platforms.
The main idea behind the spam attack is to use Flipper Zero's wireless communication capabilities to spoof advertising packets and transmit them to devices in range of pairing and connection requests.
This type of spam attack can confuse the target, make it difficult to discern between legitimate and spoofed devices, and even disrupt the user experience with non-stop notifications popping up on the targeted device.
Xtreme adds "Bluetooth spam"
Earlier this month, Flipper Xtreme announced on its Discord channel that "spam attacks" are coming in the next major firmware release.
The admins even shared a demo video showcasing a denial of service (DoS) attack on a Samsung Galaxy device, where a constant feed of connection notifications renders the device unusable.
Although the latest firmware hasn't reached stable status, the "spam attack" has been incorporated into the latest development build via a new app named 'BLE Spam,' available on GitHub.
YouTuber 'Talking Sasquach' gave the dev firmware image a spin on his Flipper Zero and reported that the attack works as expected on Windows and Android.
The BLE Spam app currently gives users eight flood attack options, including:
- Every method combined
- iOS 17 Lockup Crash
- Apple Action Modal
- Apple Device popup
- Android device pair
- Windows Device Found
Choosing any of the above causes Flipper Zero to begin broadcasting the corresponding Bluetooth packets to pop-up connectivity prompts and notifications on devices in range.
How to block these spam attacks
These attacks are more of an annoyance rather than a real threat. However, as BLE Spam allows users to craft custom notifications, these spams can get creative and trickier, playing a role in social engineering or other threat scenarios.
Android 14 and Windows 11 devices, by default, display notifications on Bluetooth connection requests, so these Flipper Zero attacks could cause problems. Thankfully, there's an easy way to block these notifications on both systems.
On Android, head to Settings → Google → Nearby Share, and turn the toggle on Show notification to the "Off" position.
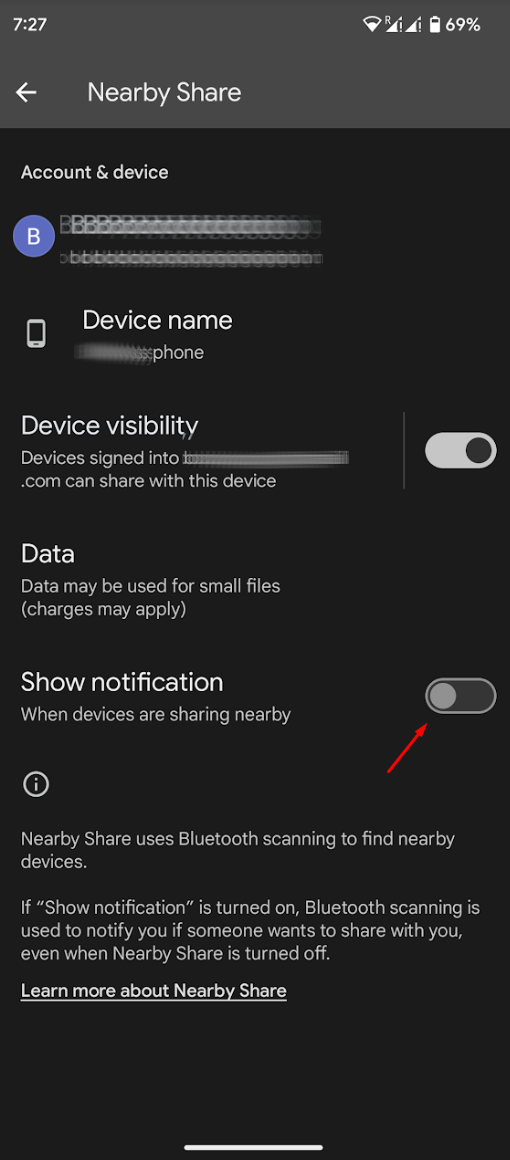
The same menu can be accessed through Settings → Connected Devices → Connection preferences → Nearby Share.
[Update 11/4] Mishaal Rahman pointed out to BleepingComputer that a more effective solution would be to disable 'Fast Pair' on Android through Settings > Google > Devices & sharing > Devices and turning off "Scan for nearby devices."
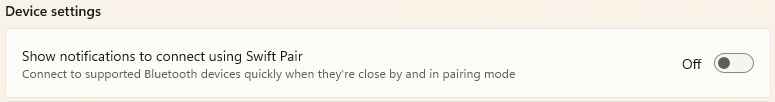
On Windows, open Settings, select 'Bluetooth & devices' from the menu on the left, then click on 'Devices,' scroll down to 'Device settings,' and turn the 'Show notifications to connect using Swift Pair' toggle to the 'Off' position.
Users shouldn't be too worried about rogue broadcasts of this kind, as these cannot perform code execution on recipient devices or cause direct harm.
However, noting the potential for phishing is crucial, and knowing how to stop the notifications in cases of persistent pranking can save people time and frustration.
Why IT teams are ditching manual patch management
Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work -- no complex scripts required.










Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now