
Elevation of privilege flaws are the most common vulnerability leveraged by corporate insiders when conducting unauthorized activities on networks, whether for malicious purposes or by downloading risky tools in a dangerous manner.
A report by Crowdstrike based on data gathered between January 2021 and April 2023 shows that insider threats are on the rise and that using privilege escalation flaws is a significant component of unauthorized activity.
According to the report, 55% of insider threats logged by the company rely on privilege escalation exploits, while the remaining 45% unwittingly introduce risks by downloading or misusing offensive tools.
Rogue insiders typically turn against their employer because they have been given financial incentives, out of spite, or due to differences with their supervisors.
CrowdStrike also categorizes incidents as insider threats when they are not malicious attacks against a company, such as using exploits to install software or perform security testing.
However, in these cases, though they are not used to attack the company, they are commonly utilized in a risky manner, potentially introducing threats or malware to the network that threat actors could abuse.
Crowdstrike has found that attacks launched from within targeted organizations cost an average of $648,000 for malicious and $485,000 for non-malicious incidents. These figures may be even higher in 2023.
Besides the significant financial cost of insider threats, Crowdstrike highlights the indirect repercussions of brand and reputation damages.
A typical insider attack
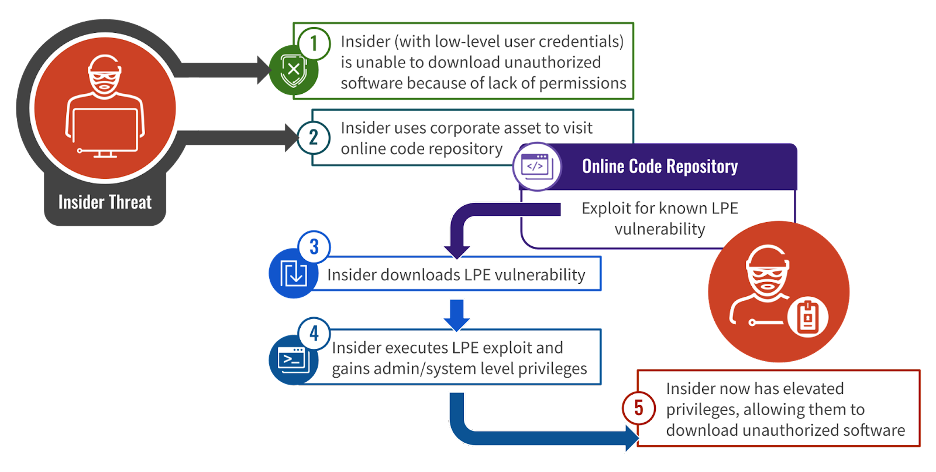
Crowdstrike explains that utilizing privilege escalation vulnerabilities to gain administrative privileges is critical to many insider attacks, as in most cases, rogue insiders start with low-level access to their network environments.
Higher privileges allow the attackers to perform actions such as downloading and installing unauthorized software, wiping logs, or even diagnosing problems on their computer using tools that require administrator privileges.
The most exploited flaws for local privilege escalation by rogue insiders are the following, according to CrowdStrike's observations:
- CVE-2017-0213: Windows flaw allows for elevating privileges through COM infrastructure exploitation.
- CVE-2022-0847 (DirtyPipe): Linux kernel pipe operations management flaw.
- CVE-2021-4034 (PwnKit): Linux flaw impacting the Polkit system service.
- CVE-2019-13272: Linux vulnerability related to improper handling of user privileges in kernel processes.
- CVE-2015-1701: Windows bug involving the kernel-mode driver 'win32k.sys' for unauthorized code execution.
- CVE-2014-4113: Also targets 'win32k.sys' but involves a different exploitation method.
The above flaws are already listed in CISA's Known Exploited Vulnerabilities Catalog (KEV) as they have been historically used in attacks by threat actors.
Even if a system has been patched for these flaws, insiders can gain elevated privileges through other means, such as DLL hijacking flaws in apps running with elevated privileges, insecure file system permissions or service configurations, or Bring Your Own Vulnerable Driver (BYOVD) attacks.
Source: Crowdstrike
Crowdstrike has seen multiple cases of exploitation of CVE-2017-0213 impacting a retail firm in Europe, where an employee downloaded an exploit via WhatsApp to install uTorrent and play games. Another case concerns a terminated employee of a media entity in the U.S.
PwnKit exploitation was observed by an employee of an Australian tech company who attempted to gain administrative rights for computer troubleshooting purposes.
An example of CVE-2015-1701 exploitation concerns a U.S. tech firm employee who attempted to bypass existing controls to install an unauthorized Java virtual machine.
While almost all of these insider threat incidents would not be considered malicious attacks, they introduce risk by modifying how a device should run or by potentially running malicious or insecure programs on the network.
Insider mistakes introduce risk
Nearly half of the insider incidents recorded by Crowdstrike concern unintentional mishaps like exploit testing getting out of control, executing offensive security tools without appropriate protection measures, and by downloading unvetted code.
For example, CrowdStrike says some incidents were caused by security professionals testing exploits and exploit kits directly on a production workstation rather than through a virtual machine that is segmented from the rest of the network.
The analysts report that most cases of this kind involve tools like the Metasploit Framework and the ElevateKit, while the vulnerabilities introduced most often as a result of careless activities are the following:
- CVE-2021-42013: Path traversal vulnerability in Apache HTTP Server 2.4.49 and 2.4.50.
- CVE-2021-4034 (PwnKit): Out-of-bounds vulnerability in Polkit system service.
- CVE-2020-0601: Spoofing vulnerability in Windows CryptoAPI.
- CVE-2016-3309: Privilege escalation issue in Windows kernel.
- CVE-2022-21999: Elevation of privilege vulnerability in Windows Print Spooler.
Introducing these flaws into corporate networks can increase the overall security risk by providing threat actors who already have a foothold in the network with additional vectors for exploitation.
However, even more important, it is not uncommon for threat actors to create fake proof-of-concept exploits or security tools that install malware on devices.
For example, in May, threat actors distributed fake Windows proof-of-concept exploits that infected devices with the Cobalt Strike backdoor.
In another attack, Rapid7 discovered that threat actors were distributing fake PoCs for zero-day exploits that installed Windows and Linux malware.
In both scenarios, installing the fake exploit on a workstation would allow initial access to a corporate network, which could lead to cyber espionage, data theft, or ransomware attacks.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now